Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
-
Siemens Desigo CC Product Family and SENTRON Powermanager
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 8.2
- ATTENTION: Low attack complexity
- Vendor: Siemens
- Equipment: Desigo CC Product Family and SENTRON Powermanager
- Vulnerability: Least Privilege Violation
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow privilege escalation.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- Desigo CC family V5.0: All versions
- Desigo CC family V5.1: All versions
- Desigo CC family V6: All versions
- Desigo CC family V7: All versions
- Desigo CC family V8: All versions
- SENTRON Powermanager V5: All versions
- SENTRON Powermanager V6: All versions
- SENTRON Powermanager V7: All versions
- SENTRON Powermanager V8: All versions
3.2 VULNERABILITY OVERVIEW
3.2.1 LEAST PRIVILEGE VIOLATION CWE-272
Wibu CodeMeter before 8.30a sometimes allows privilege escalation immediately after installation (before a logoff or reboot). For exploitation, there must have been an unprivileged installation with UAC, and the CodeMeter Control Center component must be installed, and the CodeMeter Control Center component must not have been restarted. In this scenario, the local user can navigate from Import License to a privileged instance of Windows Explorer.
CVE-2025-47809 has been assigned to this vulnerability. A CVSS v3.1 base score of 8.2 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported this vulnerability to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
Please follow below steps to update the WIBU CodeMeter :
- Uninstall the previous installed version of CodeMeter via Control Panel
- Install the CodeMeter V8.30a (Refer: https://www.wibu.com/us/support.html)
- Restart client/server after installation of CodeMeter
For more details regarding the vulnerability in CodeMeter Runtime refer to:
- WIBU Systems Security Advisory WIBU-100120: https://www.wibu.com/support/security-advisories/wibu-100120.html
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-201595 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting this vulnerability has been reported to CISA at this time. This vulnerability is not exploitable remotely.
5. UPDATE HISTORY
- August 19, 2025: Initial Republication of Siemens ProductCERT SSA-201595
-
Siemens Mendix SAML Module
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 8.7
- ATTENTION: Exploitable remotely
- Vendor: Siemens
- Equipment: Mendix SAML Module
- Vulnerability: Improper Verification of Cryptographic Signature
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow unauthenticated remote attackers to hijack an account in specific SSO configurations.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- Siemens Mendix SAML (Mendix 9.24 compatible): Versions prior to V3.6.21
- Siemens Mendix SAML (Mendix 10.12 compatible): Versions prior to V4.0.3
- Siemens Mendix SAML (Mendix 10.21 compatible): Versions prior to V4.1.2
3.2 VULNERABILITY OVERVIEW
3.2.1 IMPROPER VERIFICATION OF CRYPTOGRAPHIC SIGNATURE CWE-347
Affected versions of the module insufficiently enforce signature validation and binding checks. This could allow unauthenticated remote attackers to hijack an account in specific SSO configurations.
CVE-2025-40758 has been assigned to this vulnerability. A CVSS v3.1 base score of 8.7 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:N).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported this vulnerability to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- All affected products: Make sure to use configurations where UseEncryption is enabled
- Mendix SAML (Mendix 9.24 compatible): Update to V3.6.21 or later version
- Mendix SAML (Mendix 10.12 compatible): Update to V4.0.3 or later version
- Mendix SAML (Mendix 10.21 compatible): Update to V4.1.2 or later version
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-395458 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting this vulnerability has been reported to CISA at this time. This vulnerability has a high attack complexity.
5. UPDATE HISTORY
- August 19, 2025: Initial Republication of Siemens ProductCERT SSA-395458
-
CISA Releases Four Industrial Control Systems Advisories
CISA released four Industrial Control Systems (ICS) advisories on August 19, 2025. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS.
- ICSA-25-231-01 Siemens Desigo CC Product Family and SENTRON Powermanager
- ICSA-25-231-02 Siemens Mendix SAML Module
- ICSA-25-217-02 Tigo Energy Cloud Connect Advanced (Update A)
- ICSA-25-219-07 EG4 Electronics EG4 Inverters (Update A)
CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations.
-
CISA Adds One Known Exploited Vulnerability to Catalog
CISA has added one new vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog, based on evidence of active exploitation.
- CVE-2025-54948 Trend Micro Apex One OS Command Injection Vulnerability
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the KEV Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of KEV Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria.
-
Mobile Phishers Target Brokerage Accounts in ‘Ramp and Dump’ Cashout Scheme
Cybercriminal groups peddling sophisticated phishing kits that convert stolen card data into mobile wallets have recently shifted their focus to targeting customers of brokerage services, new research shows. Undeterred by security controls at these trading platforms that block users from wiring funds directly out of accounts, the phishers have pivoted to using multiple compromised brokerage accounts in unison to manipulate the prices of foreign stocks.
Image: Shutterstock, WhataWin.
This so-called ‘ramp and dump‘ scheme borrows its name from age-old “pump and dump” scams, wherein fraudsters purchase a large number of shares in some penny stock, and then promote the company in a frenzied social media blitz to build up interest from other investors. The fraudsters dump their shares after the price of the penny stock increases to some degree, which usually then causes a sharp drop in the value of the shares for legitimate investors.
With ramp and dump, the scammers do not need to rely on ginning up interest in the targeted stock on social media. Rather, they will preposition themselves in the stock that they wish to inflate, using compromised accounts to purchase large volumes of it and then dumping the shares after the stock price reaches a certain value. In February 2025, the FBI said it was seeking information from victims of this scheme.
“In this variation, the price manipulation is primarily the result of controlled trading activity conducted by the bad actors behind the scam,” reads an advisory from the Financial Industry Regulatory Authority (FINRA), a private, non-profit organization that regulates member brokerage firms. “Ultimately, the outcome for unsuspecting investors is the same—a catastrophic collapse in share price that leaves investors with unrecoverable losses.”
Ford Merrill is a security researcher at SecAlliance, a CSIS Security Group company. Merrill said he has tracked recent ramp-and-dump activity to a bustling Chinese-language community that is quite openly selling advanced mobile phishing kits on Telegram.
“They will often coordinate with other actors and will wait until a certain time to buy a particular Chinese IPO [initial public offering] stock or penny stock,” said Merrill, who has been chronicling the rapid maturation and growth of the China-based phishing community over the past three years.
“They’ll use all these victim brokerage accounts, and if needed they’ll liquidate the account’s current positions, and will preposition themselves in that instrument in some account they control, and then sell everything when the price goes up,” he said. “The victim will be left with worthless shares of that equity in their account, and the brokerage may not be happy either.”
Merrill said the early days of these phishing groups — between 2022 and 2024 — were typified by phishing kits that used text messages to spoof the U.S. Postal Service or some local toll road operator, warning about a delinquent shipping or toll fee that needed paying. Recipients who clicked the link and provided their payment information at a fake USPS or toll operator site were then asked to verify the transaction by sharing a one-time code sent via text message.
In reality, the victim’s bank is sending that code to the mobile number on file for their customer because the fraudsters have just attempted to enroll that victim’s card details into a mobile wallet. If the visitor supplies that one-time code, their payment card is then added to a new mobile wallet on an Apple or Google device that is physically controlled by the phishers.
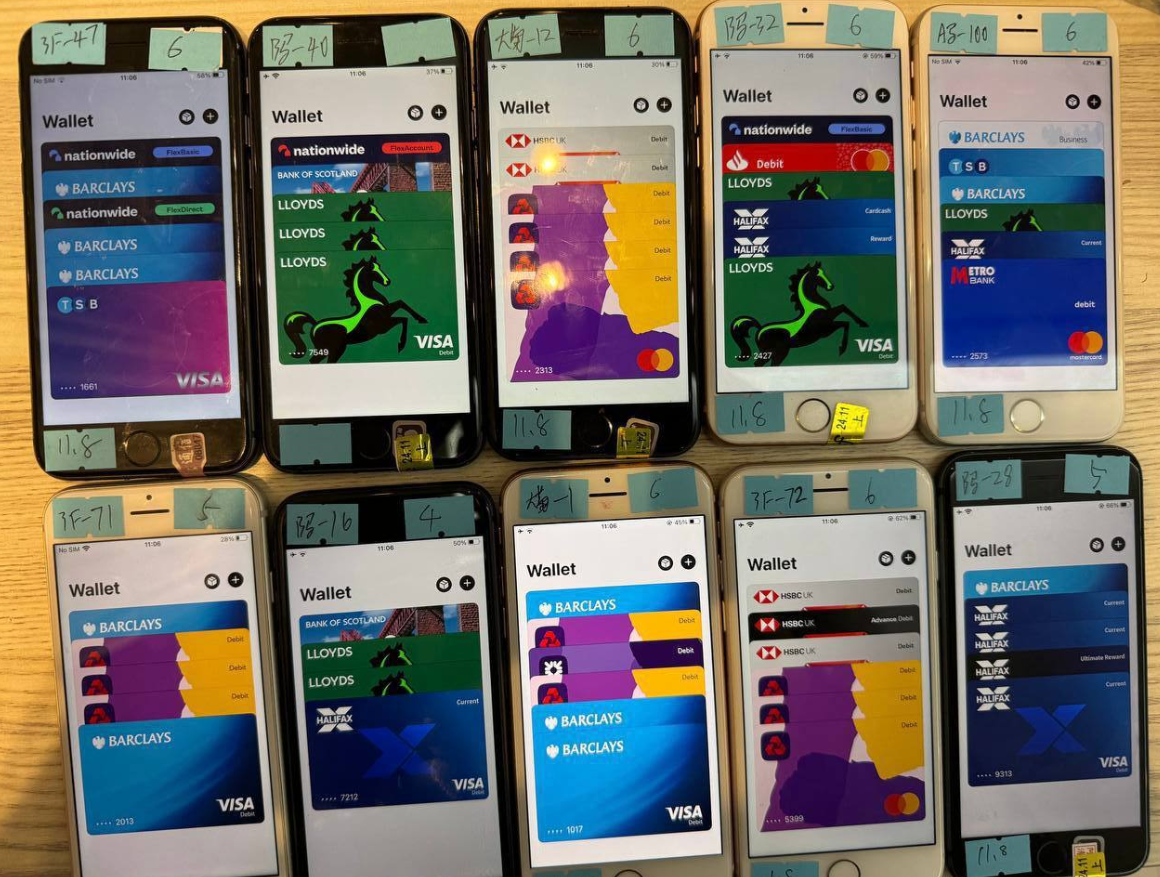
The phishing gangs typically load multiple stolen cards to digital wallets on a single Apple or Android device, and then sell those phones in bulk to scammers who use them for fraudulent e-commerce and tap-to-pay transactions.
An image from the Telegram channel for a popular Chinese mobile phishing kit vendor shows 10 mobile phones for sale, each loaded with 4-6 digital wallets from different financial institutions.
This China-based phishing collective exposed a major weakness common to many U.S.-based financial institutions that already require multi-factor authentication: The reliance on a single, phishable one-time token for provisioning mobile wallets. Happily, Merrill said many financial institutions that were caught flat-footed on this scam two years ago have since strengthened authentication requirements for onboarding new mobile wallets (such as requiring the card to be enrolled via the bank’s mobile app).
But just as squeezing one part of a balloon merely forces the air trapped inside to bulge into another area, fraudsters don’t go away when you make their current enterprise less profitable: They just shift their focus to a less-guarded area. And lately, that gaze has settled squarely on customers of the major brokerage platforms, Merrill said.
THE OUTSIDER
Merrill pointed to several Telegram channels operated by some of the more accomplished phishing kit sellers, which are full of videos demonstrating how every feature in their kits can be tailored to the attacker’s target. The video snippet below comes from the Telegram channel of “Outsider,” a popular Mandarin-speaking phishing kit vendor whose latest offering includes a number of ready-made templates for using text messages to phish brokerage account credentials and one-time codes.
According to Merrill, Outsider is a woman who previously went by the handle “Chenlun.” KrebsOnSecurity profiled Chenlun’s phishing empire in an October 2023 story about a China-based group that was phishing mobile customers of more than a dozen postal services around the globe. In that case, the phishing sites were using a Telegram bot that sent stolen credentials to the “@chenlun” Telegram account.
Chenlun’s phishing lures are sent via Apple’s iMessage and Google’s RCS service and spoof one of the major brokerage platforms, warning that the account has been suspended for suspicious activity and that recipients should log in and verify some information. The missives include a link to a phishing page that collects the customer’s username and password, and then asks the user to enter a one-time code that will arrive via SMS.
The new phish kit videos on Outsider’s Telegram channel only feature templates for Schwab customers, but Merrill said the kit can easily be adapted to target other brokerage platforms. One reason the fraudsters are picking on brokerage firms, he said, has to do with the way they handle multi-factor authentication.
Schwab clients are presented with two options for second factor authentication when they open an account. Users who select the option to only prompt for a code on untrusted devices can choose to receive it via text message, an automated inbound phone call, or an outbound call to Schwab. With the “always at login” option selected, users can choose to receive the code through the Schwab app, a text message, or a Symantec VIP mobile app.
In response to questions, Schwab said it regularly updates clients on emerging fraud trends, including this specific type, which the company addressed in communications sent to clients earlier this year.
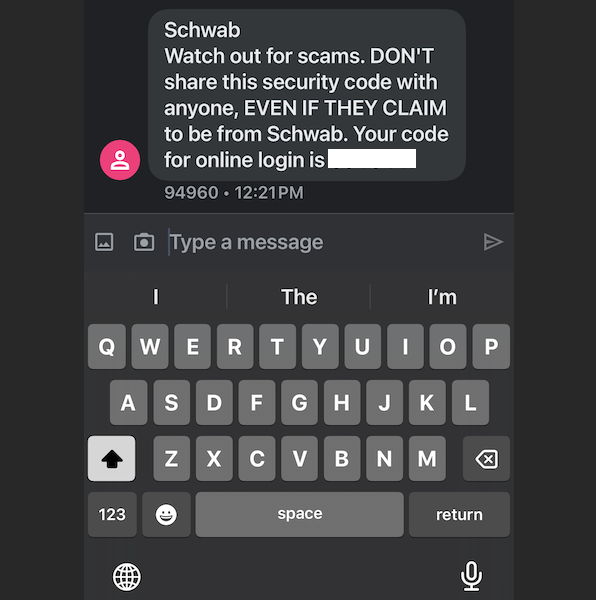
The 2FA text message from Schwab warns recipients against giving away their one-time code.
“That message focused on trading-related fraud, highlighting both account intrusions and scams conducted through social media or messaging apps that deceive individuals into executing trades themselves,” Schwab said in a written statement. “We are aware and tracking this trend across several channels, as well as others like it, which attempt to exploit SMS-based verification with stolen credentials. We actively monitor for suspicious patterns and take steps to disrupt them. This activity is part of a broader, industry-wide threat, and we take a multi-layered approach to address and mitigate it.”
Other popular brokerage platforms allow similar methods for multi-factor authentication. Fidelity requires a username and password on initial login, and offers the ability to receive a one-time token via SMS, an automated phone call, or by approving a push notification sent through the Fidelity mobile app. However, all three of these methods for sending one-time tokens are phishable; even with the brokerage firm’s app, the phishers could prompt the user to approve a login request that they initiated in the app with the phished credentials.
Vanguard offers customers a range of multi-factor authentication choices, including the option to require a physical security key in addition to one’s credentials on each login. A security key implements a robust form of multi-factor authentication known as Universal 2nd Factor (U2F), which allows the user to complete the login process simply by connecting an enrolled USB or Bluetooth device and pressing a button. The key works without the need for any special software drivers, and the nice thing about it is your second factor cannot be phished.
THE PERFECT CRIME?
Merrill said that in many ways the ramp-and-dump scheme is the perfect crime because it leaves precious few connections between the victim brokerage accounts and the fraudsters.
“It’s really genius because it decouples so many things,” he said. “They can buy shares [in the stock to be pumped] in their personal account on the Chinese exchanges, and the price happens to go up. The Chinese or Hong Kong brokerages aren’t going to see anything funky.”
Merrill said it’s unclear exactly how those perpetrating these ramp-and-dump schemes coordinate their activities, such as whether the accounts are phished well in advance or shortly before being used to inflate the stock price of Chinese companies. The latter possibility would fit nicely with the existing human infrastructure these criminal groups already have in place.
For example, KrebsOnSecurity recently wrote about research from Merrill and other researchers showing the phishers behind these slick mobile phishing kits employed people to sit for hours at a time in front of large banks of mobile phones being used to send the text message lures. These technicians were needed to respond in real time to victims who were supplying the one-time code sent from their financial institution.

The ashtray says: You’ve been phishing all night.
“You can get access to a victim’s brokerage with a one-time passcode, but then you sort of have to use it right away if you can’t set new security settings so you can come back to that account later,” Merrill said.
The rapid pace of innovations produced by these China-based phishing vendors is due in part to their use of artificial intelligence and large language models to help develop the mobile phishing kits, he added.
“These guys are vibe coding stuff together and using LLMs to translate things or help put the user interface together,” Merrill said. “It’s only a matter of time before they start to integrate the LLMs into their development cycle to make it more rapid. The technologies they are building definitely have helped lower the barrier of entry for everyone.”
-
Siemens COMOS
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 8.2
- ATTENTION: Low Attack Complexity
- Vendor: Siemens
- Equipment: COMOS
- Vulnerability: Out-of-bounds Write
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an attacker to cause a crash, potentially enabling a denial-of-service attack (Crash, Exit, or Restart) or possible code execution.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- Siemens COMOS: all versions prior to V10.6
3.2 VULNERABILITY OVERVIEW
3.2.1 OUT-OF-BOUNDS WRITE CWE-787
Out-of-bounds Write vulnerability was discovered in Open Design Alliance Drawings SDK before 2025.10. Reading crafted DWF file and missing proper checks on received SectionIterator data can trigger an unhandled exception. This can allow attackers to cause a crash, potentially enabling a denial-of-service attack (Crash, Exit, or Restart) or possible code execution.
CVE-2024-8894 has been assigned to this vulnerability. A CVSS v3.1 base score of 8.2 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens ProductCERT reported this vulnerability to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- COMOS: Ensure all files imported into the affected product originate from a trusted source and are transmitted over secure channels
- COMOS: Update to V10.6 or later version
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-769791 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting this vulnerability has been reported to CISA at this time. This vulnerability is not exploitable remotely.
5. UPDATE HISTORY
- August 14, 2025: Initial Republication of Siemens ProductCERT SSA-769791
-
Siemens SIPROTEC 5
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v4 2.4
- ATTENTION: Low attack complexity
- Vendor: Siemens
- Equipment: SIPROTEC 5
- Vulnerability: Allocation of Resources Without Limits or Throttling
2. RISK EVALUATION
Successful exploitation of this vulnerability could allow an attacker with physical access to send specially crafted packets with high bandwidth to the affected devices thus forcing them to exhaust their memory and stop responding to any network traffic via the local USB port.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- SIPROTEC 5 6MD84 (CP300): Versions prior to V10.0
- SIPROTEC 5 7SD82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SD86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SD87 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SJ81 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SJ82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SJ85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SJ86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SK82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SK85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SL82 (CP150): Versions prior to V10.0
- SIPROTEC 5 6MD85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SL86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SL87 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SS85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7ST85 (CP300): Versions prior to V10.0
- SIPROTEC 5 7ST86 (CP300): Versions prior to V10.0
- SIPROTEC 5 7SX82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SX85 (CP300): Versions prior to V10.0
- SIPROTEC 5 7SY82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7UM85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7UT82 (CP150): Versions prior to V10.0
- SIPROTEC 5 6MD86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7UT85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7UT86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7UT87 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7VE85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7VK87 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7VU85 (CP300): Versions prior to V10.0
- SIPROTEC 5 Compact 7SX800 (CP050): Versions prior to V10.0
- SIPROTEC 5 6MD89 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 6MU85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7KE85 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SA82 (CP150): Versions prior to V10.0
- SIPROTEC 5 7SA86 (CP300): Versions V7.80 up to but not including V10.0
- SIPROTEC 5 7SA87 (CP300): Versions V7.80 up to but not including V10.0
3.2 VULNERABILITY OVERVIEW
3.2.1 ALLOCATION OF RESOURCES WITHOUT LIMITS OR THROTTLING CWE-770
Affected devices do not properly limit the bandwidth for incoming network packets over their local USB port. This could allow an attacker with physical access to send specially crafted packets with high bandwidth to the affected devices thus forcing them to exhaust their memory and stop responding to any network traffic via the local USB port. Affected devices reset themselves automatically after a successful attack. The protection function is not affected of this vulnerability.
CVE-2025-40570 has been assigned to this vulnerability. A CVSS v3.1 base score of 2.4 has been calculated; the CVSS vector string is (CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L).
A CVSS v4 score has also been calculated for CVE-2025-40570. A base score of 2.4 has been calculated; the CVSS vector string is (CVSS:4.0/AV:P/AC:L/AT:N/PR:N/UI:N/VC:N/VI:N/VA:L/SC:N/SI:N/SA:N).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported this vulnerability to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- SIPROTEC 5 6MD84 (CP300), SIPROTEC 5 6MD85 (CP300), SIPROTEC 5 6MD86 (CP300), SIPROTEC 5 6MD89 (CP300), SIPROTEC 5 6MU85 (CP300), SIPROTEC 5 7KE85 (CP300), SIPROTEC 5 7SA86 (CP300), SIPROTEC 5 7SA87 (CP300), SIPROTEC 5 7SD86 (CP300), SIPROTEC 5 7SD87 (CP300), SIPROTEC 5 7SJ85 (CP300), SIPROTEC 5 7SJ86 (CP300), SIPROTEC 5 7SK85 (CP300), SIPROTEC 5 7SL86 (CP300), SIPROTEC 5 7SL87 (CP300), SIPROTEC 5 7SS85 (CP300), SIPROTEC 5 7ST85 (CP300), SIPROTEC 5 7ST86 (CP300), SIPROTEC 5 7SX85 (CP300), SIPROTEC 5 7UM85 (CP300), SIPROTEC 5 7UT85 (CP300), SIPROTEC 5 7UT86 (CP300), SIPROTEC 5 7UT87 (CP300), SIPROTEC 5 7VE85 (CP300), SIPROTEC 5 7VK87 (CP300), SIPROTEC 5 7VU85 (CP300): Update to V10.0 or later version
- SIPROTEC 5 7SA82 (CP150), SIPROTEC 5 7SD82 (CP150), SIPROTEC 5 7SJ81 (CP150), SIPROTEC 5 7SJ82 (CP150), SIPROTEC 5 7SK82 (CP150), SIPROTEC 5 7SL82 (CP150), SIPROTEC 5 7SX82 (CP150), SIPROTEC 5 7SY82 (CP150), SIPROTEC 5 7UT82 (CP150): Update to V10.0 or later version
- SIPROTEC 5 Compact 7SX800 (CP050): Update to V10.0 or later version
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage.
For more information see the associated Siemens security advisory SSA-894058 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of this vulnerability, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting this vulnerability has been reported to CISA at this time. This vulnerability is not exploitable remotely.
5. UPDATE HISTORY
- August 14, 2025: Initial Republication of Siemens ProductCERT SSA-894058
-
Siemens RUGGEDCOM CROSSBOW Station Access Controller
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v4 6.9
- ATTENTION: Exploitable remotely/low attack complexity
- Vendor: Siemens
- Equipment: RUGGEDCOM CROSSBOW Station Access Controller (SAC)
- Vulnerabilities: Heap-Based Buffer Overflow, Integer Overflow or Wraparound
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could allow an attacker to execute arbitrary code or create a denial-of-service condition.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- RUGGEDCOM CROSSBOW Station Access Controller (SAC): Versions prior to V5.7
3.2 VULNERABILITY OVERVIEW
3.2.1 HEAP-BASED BUFFER OVERFLOW CWE-122
An integer overflow can be triggered in SQLite’s ‘concat_ws()’ function. The resulting, truncated integer is then used to allocate a buffer. When SQLite then writes the resulting string to the buffer, it uses the original, untruncated size and thus a wild Heap Buffer overflow of size 4GB can be triggered. This can result in arbitrary code execution.
CVE-2025-3277 has been assigned to this vulnerability. A CVSS v3.1 base score of 8.3 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:L/A:L).
A CVSS v4 score has also been calculated for CVE-2025-3277. A base score of 6.9 has been calculated; the CVSS vector string is (CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:L/VI:L/VA:L/SC:L/SI:L/SA:L).
3.2.2 INTEGER OVERFLOW OR WRAPAROUND CWE-190
In SQLite, the concat_ws() SQL function can cause memory to be written beyond the end of a malloc-allocated buffer. If the separator argument is attacker-controlled and has a large string (e.g., 2MB or more), an integer overflow occurs in calculating the size of the result buffer, and thus malloc may not allocate enough memory.
CVE-2025-29087 has been assigned to this vulnerability. A CVSS v3.1 base score of 5.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H).
3.2.3 INTEGER OVERFLOW OR WRAPAROUND CWE-190
A vulnerability in sqlite allows an attacker to cause a denial-of-service via the SQLITE_DBCONFIG_LOOKASIDE component.
CVE-2025-29088 has been assigned to this vulnerability. A CVSS v3.1 base score of 7.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported these vulnerabilities to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- RUGGEDCOM CROSSBOW Station Access Controller (SAC): Update to V5.7 or later version
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage.
For more information see the associated Siemens security advisory SSA-994087 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting these vulnerabilities has been reported to CISA at this time.
5. UPDATE HISTORY
- August 14, 2025: Initial Republication of Siemens ProductCERT SSA-994087
-
Siemens Opcenter Quality
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens’ ProductCERT Security Advisories (CERT Services | Services | Siemens Global).
1. EXECUTIVE SUMMARY
- CVSS v3 7.1
- ATTENTION: Exploitable from adjacent network/low attack complexity
- Vendor: Siemens
- Equipment: Opcenter Quality
- Vulnerabilities: Incorrect Authorization, Missing Encryption of Sensitive Data, Generation of Error Message Containing Sensitive Information, Insufficient Session Expiration, Use of a Broken or Risky Cryptographic Algorithm
2. RISK EVALUATION
Successful exploitation of these vulnerabilities could allow an attacker to gain complete access of the application, access to sensitive information, access to session information, or execute a Machine-In-The-Middle attack and compromise confidentiality and integrity of data.
3. TECHNICAL DETAILS
3.1 AFFECTED PRODUCTS
Siemens reports that the following products are affected:
- Siemens SmartClient modules Opcenter QL Home (SC): Versions between 13.2 and 2506
- Siemens SOA Audit: Versions between 13.2 and 2506
- Siemens SOA Cockpit: Versions between 13.2 and 2506
3.2 VULNERABILITY OVERVIEW
3.2.1 INCORRECT AUTHORIZATION CWE-863
The affected application does not enforce mandatory authorization on some functionality level at server side. This could allow an authenticated attacker to gain complete access of the application.
CVE-2024-41979 has been assigned to this vulnerability. A CVSS v3.1 base score of 7.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H).
3.2.2 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The affected application do not encrypt the communication in LDAP interface by default. This could allow an authenticated attacker to gain unauthorized access to sensitive information.
CVE-2024-41980 has been assigned to this vulnerability. A CVSS v3.1 base score of 3.1 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:H/UI:N/S:U/C:L/I:L/A:N).
3.2.3 MISSING ENCRYPTION OF SENSITIVE DATA CWE-311
The affected application does not have adequate encryption of sensitive information. This could allow an authenticated attacker to gain access of sensitive information.
CVE-2024-41982 has been assigned to this vulnerability. A CVSS v3.1 base score of 4.8 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:L/UI:N/S:U/C:H/I:N/A:N).
3.2.4 GENERATION OF ERROR MESSAGE CONTAINING SENSITIVE INFORMATION CWE-209
The affected application displays SQL statement in the error messages encountered during the generation of reports using Cockpit tool.
CVE-2024-41983 has been assigned to this vulnerability. A CVSS v3.1 base score of 3.5 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N).
3.2.5 GENERATION OF ERROR MESSAGE CONTAINING SENSITIVE INFORMATION CWE-209
The affected application improperly handles error while accessing an inaccessible resource leading to exposing the system applications.
CVE-2024-41984 has been assigned to this vulnerability. A CVSS v3.1 base score of 2.6 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:N/UI:R/S:U/C:L/I:N/A:N).
3.2.6 INSUFFICIENT SESSION EXPIRATION CWE-613
The affected application does not expire the session without logout. This could allow an attacker to get unauthorized access if the session is left idle.
CVE-2024-41985 has been assigned to this vulnerability. A CVSS v3.1 base score of 2.6 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:N/UI:R/S:U/C:N/I:L/A:N).
3.2.7 USE OF A BROKEN OR RISKY CRYPTOGRAPHIC ALGORITHM CWE-327
The affected application support insecure TLS 1.0 and 1.1 protocol. An attacker could achieve a man-in-the-middle attack and compromise confidentiality and integrity of data.
CVE-2024-41986 has been assigned to this vulnerability. A CVSS v3.1 base score of 6.4 has been calculated; the CVSS vector string is (CVSS:3.1/AV:A/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:L).
3.3 BACKGROUND
- CRITICAL INFRASTRUCTURE SECTORS: Critical Manufacturing
- COUNTRIES/AREAS DEPLOYED: Worldwide
- COMPANY HEADQUARTERS LOCATION: Germany
3.4 RESEARCHER
Siemens reported these vulnerabilities to CISA.
4. MITIGATIONS
Siemens has identified the following specific workarounds and mitigations users can apply to reduce risk:
- All affected products: Update to V2506 or later version
- (CVE-2024-41979) All affected products: The SmartClient should be operated in a secured network and context only
- (CVE-2024-41979) All affected products: Remove all tools giving possibility to call SOAP-services outside from the SmartClient
- (CVE-2024-41979) All affected products: The hardening instructions mentioned in the products security concept should be followed
- (CVE-2024-41980) All affected products: Harden LDAP-interface secure protocols by enabling the SSL-flag on configuration and a proper setup of your TLS-configuration
- (CVE-2024-41980) All affected products: All the users (including in LDAP) should be given the least privileges required
- (CVE-2024-41982) All affected products: Limit the permission to access those fields using the least privilege strategy
- (CVE-2024-41983) All affected products: Do not use original table structures and accounts for reporting. Create your own reporting accounts which have access via synonyms forwarding on views representing access to result-sets the user may use for evaluation
- (CVE-2024-41983) All affected products: Use DB-tools to limit load on productive systems for reporting accounts or use offline systems for reporting
- (CVE-2024-41983) All affected products: Harden your IIS
- (CVE-2024-41983) All affected products: Prevent any scanning of structures and configurations
- (CVE-2024-41983) All affected products: Limit the information to prevent to the end-user based on the need-to-know-principle to the minimum possible information
- (CVE-2024-41984) All affected products: Hardening of the solution, including the OS and IIS, is required, with specific measures such as hiding the IIS version to enhance security
- (CVE-2024-41984) All affected products: Users should not have the possibility to scan folders and extensions of files allowed to open should be limited to the required one
- (CVE-2024-41986) All affected products: Disable all protocols (SSL v2/v3, TLS 1.0, TLS 1.1) the solution should not use.
- (CVE-2024-41986) All affected products: Ensure, TLS 1.2 is enabled if you plan to use TLS 1.2.
- (CVE-2024-41986) All affected products: Follow the instructions of the security concept of Opcenter Quality and vendors.
As a general security measure, Siemens recommends protecting network access to devices with appropriate mechanisms. To operate the devices in a protected IT environment, Siemens recommends configuring the environment according to Siemens’ operational guidelines for industrial security and following recommendations in the product manuals.
Additional information on industrial security by Siemens can be found on the Siemens industrial security webpage
For more information see the associated Siemens security advisory SSA-382999 in HTML and CSAF.
CISA recommends users take defensive measures to minimize the risk of exploitation of these vulnerabilities, such as:
- Minimize network exposure for all control system devices and/or systems, ensuring they are not accessible from the internet.
- Locate control system networks and remote devices behind firewalls and isolating them from business networks.
- When remote access is required, use more secure methods, such as Virtual Private Networks (VPNs). Recognize VPNs may have vulnerabilities, should be updated to the most recent version available, and are only as secure as the connected devices.
CISA reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
CISA also provides a section for control systems security recommended practices on the ICS webpage on cisa.gov. Several CISA products detailing cyber defense best practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
CISA encourages organizations to implement recommended cybersecurity strategies for proactive defense of ICS assets.
Additional mitigation guidance and recommended practices are publicly available on the ICS webpage at cisa.gov in the technical information paper, ICS-TIP-12-146-01B–Targeted Cyber Intrusion Detection and Mitigation Strategies.
Organizations observing suspected malicious activity should follow established internal procedures and report findings to CISA for tracking and correlation against other incidents.
CISA also recommends users take the following measures to protect themselves from social engineering attacks:
- Do not click web links or open attachments in unsolicited email messages.
- Refer to Recognizing and Avoiding Email Scams for more information on avoiding email scams.
- Refer to Avoiding Social Engineering and Phishing Attacks for more information on social engineering attacks.
No known public exploitation specifically targeting these vulnerabilities has been reported to CISA at this time. These vulnerabilities are not exploitable remotely.
5. UPDATE HISTORY
- August 14, 2025: Initial Republication of Siemens ProductCERT SSA-382999